Step 1: Generate an HMAC Signature
Use the secret key from your console to generate an HMAC-SHA256 signature for each user.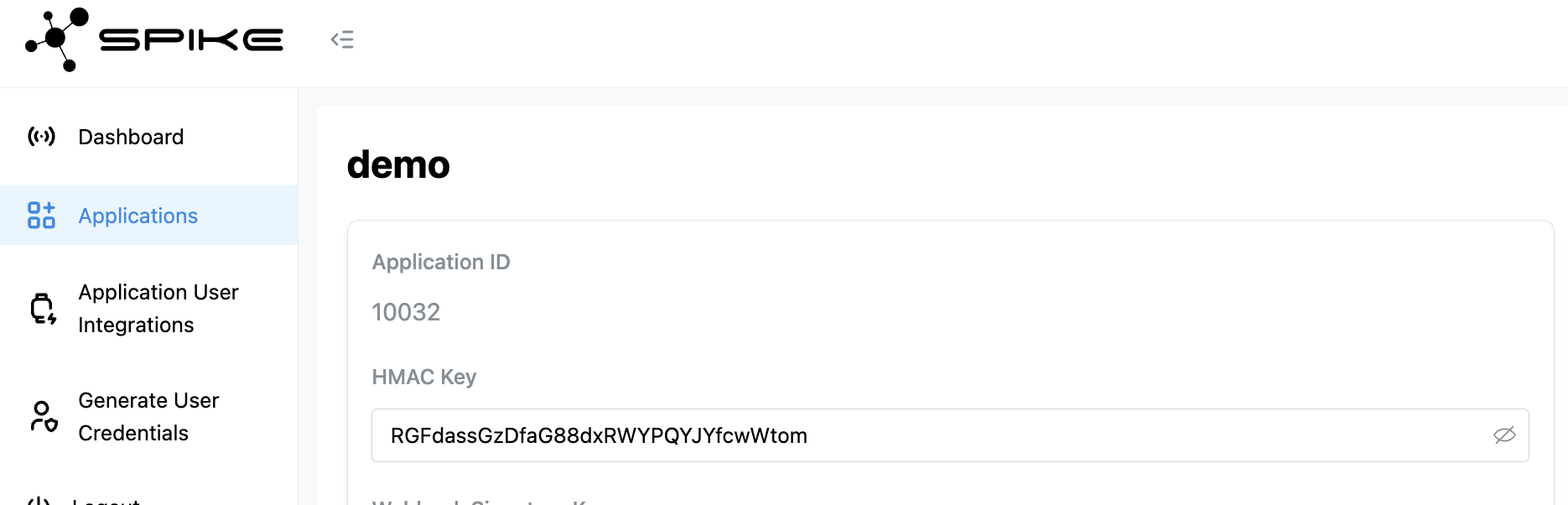
Code Examples
Step 2: Exchange Signature for Access Token
Send the generated signature to the following endpoint to authorize the user and get an access token:https://app-api.spikeapi.com/v3/auth/hmac
Request Parameters
The ID of the application for which you are requesting the access token.
The unique ID of the user in your system. This is the only identifier needed
to reference the user. Maximum 1-128 alphanumeric characters. May include
these special characters: - _ .
The HMAC signature generated to verify the user’s authenticity.
Example Request
Response
The access token for the user. Must be consistent throughout the user’s
lifecycle. No pre-registration is required—users are valid after the first
provider integration.
Example Response
Step 3: Store and Use the Access Token
On successful authentication, the API will return an access token in the response. Store this token securely and include it in the Authorization header for all subsequent API calls:Authorization: Bearer <access_token>
